prerequirements: ASA software 9.8.1 (I have tested 9.8.2)
Azure configuration:
add a Virtual network gateway to you azure subnet, I use basic, then adding a connection to the gateway like this:
venus3444 alex adams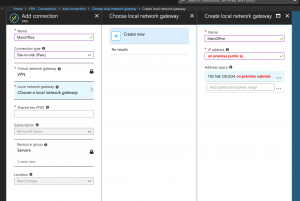
ASA configuration
Configure VPN interface:
crypto ikev2 policy 3 encryption aes-256 integrity sha group 2 prf sha lifetime seconds 10800 crypto ipsec ikev2 ipsec-proposal Proposal-Azure protocol esp encryption aes-256 protocol esp integrity sha-1 crypto ipsec profile Profile-Azure set ikev2 ipsec-proposal Proposal-Azure set pfs group2 set security-association lifetime kilobytes 102400000 set security-association lifetime seconds 10800 interface Tunnel1 nameif VPN-AZURE ip address 169.254.2.1 255.255.255.0 standby 169.254.2.2 tunnel source interface outside tunnel destination [Azure vpngateway public ip] tunnel mode ipsec ipv4 tunnel protection ipsec profile Profile-Azure tunnel-group [Azure vpngateway public ip] type ipsec-l2l tunnel-group [Azure vpngateway public ip] ipsec-attributes ikev2 remote-authentication pre-shared-key [PreesharedKey] ikev2 local-authentication pre-shared-key [PreesharedKey]
Configure static route to azure networks:
route VPN-AZURE [local azure subnet scope] 255.255.255.0 [Azure vpngateway public ip] 1
Source:
https://supportforums.cisco.com/t5/vpn/route-based-vpn-vti-for-asa-finally-here/td-p/3046928
